Enhancing Mobile Security: The BAP Certification and OWASP Mobile Top 10
Thehackingverse | Security Researcher @bugdetector
12/8/20242 min read


Introduction to BAP Certification
The world of mobile applications is rapidly evolving, and so are the threats associated with them. To combat these threats, cybersecurity professionals are increasingly turning to specialized certifications like the BAP (Budgeting Android Pentester) certification. This certification not only equips individuals with essential pentesting skills but also emphasizes a thorough understanding of the OWASP Mobile Top 10 vulnerabilities. As mobile devices become ubiquitous, the demand for certified professionals who can identify and mitigate mobile security risks has never been greater.
Understanding OWASP Mobile Top 10 Vulnerabilities
The OWASP Mobile Top 10 is a crucial framework that outlines the most pressing security vulnerabilities faced by mobile applications. It serves as a guide for developers and security professionals alike, ensuring they are aware of these risks and can take appropriate measures to safeguard user data. Here’s a brief overview of the key categories:
Improper Platform Usage: This includes failures in using platform features securely and can lead to unauthorized access.
Insecure Data Storage: Sensitive information stored locally might be vulnerable to external access if not properly encrypted.
Insecure Communication: Unprotected data transmission can expose information to interception.
Insecure Authentication: Weak authentication processes allow attackers to impersonate legitimate users.
Insufficient Cryptography: Inadequately implemented cryptographic algorithms can compromise data confidentiality.
Insecure Authorization: Weak authorization processes allow attackers to gain privileges users /access sensitive information.
Client Code Quality : The business impact from this category of vulnerabilities varies greatly, depending upon the nature of the exploit. Poor code quality issues that result in remote code execution could lead to the following business impacts i.e.
Information Theft;
Reputational Damage;
Intellectual Property Theft
Code Tampering: Attackers may exploit vulnerable apps to alter their code, potentially affecting user experience and security.
Reverse Engineering: Compromising the app code facilitates attacks and exploits sensitive information.
Extraneous Functionality: Unused features may present security holes that can be exploited by attackers.
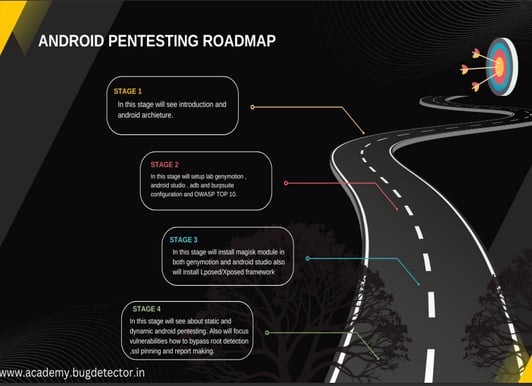
The Journey to BAP Certification
Obtaining the BAP certification involves a commitment to studying mobile security extensively, including the OWASP Mobile Top 10 vulnerabilities. The certification process typically includes a rigorous examination, practical applications, and case studies that challenge candidates to identify security flaws in real-world scenarios.
Professionals who achieve the BAP certification not only enhance their skill sets but also add significant value to their teams and organizations. They become pivotal in ensuring that mobile applications are developed and maintained with security as a top priority.
Conclusion
In conclusion, the BAP certification is a vital asset for anyone in the cybersecurity field focusing on mobile application security. By aligning their skills with the OWASP Mobile Top 10 framework, certified professionals are better equipped to protect against pervasive vulnerabilities. As mobile usage continues to grow, so does the necessity for skilled pentesters to uphold application integrity and user trust.

Bug Detectors
You Build We Hack !
We are team of security researcher's where we are helping the industry via providing the security consultancy and training with the prior experience of our researcher's in order to keep them secure.
Connect with us
Join our academy
info@bugdetector.in
+91 8178925263
© 2025. All rights reserved.

